Last updated on August 15, 2021
The term Social engineering defines a wide range of malicious activities that involve human interactions, which consist of misleading the innocent tactfully to make mistakes, give out user credentials and the confidential personal information.
In today’s world, social engineering is recognized as a technique that criminals and cyber-crooks use to trick users into exposing confidential information, which is supposed to be kept safely unless that is requested by a relevant app for security purpose or verification.
The ‘social engineers’ (can be used as a professional term for a ‘hacker’) collect those data in order to gain access to various systems and apps (e.g. Facebook, Email, Imo, other social networking modes) making it easier for them to control over till they get the targeted benefit. This benefit can be something earned through blackmailing the users, who are not rational enough.

The following cycle shows how the attacks take place.
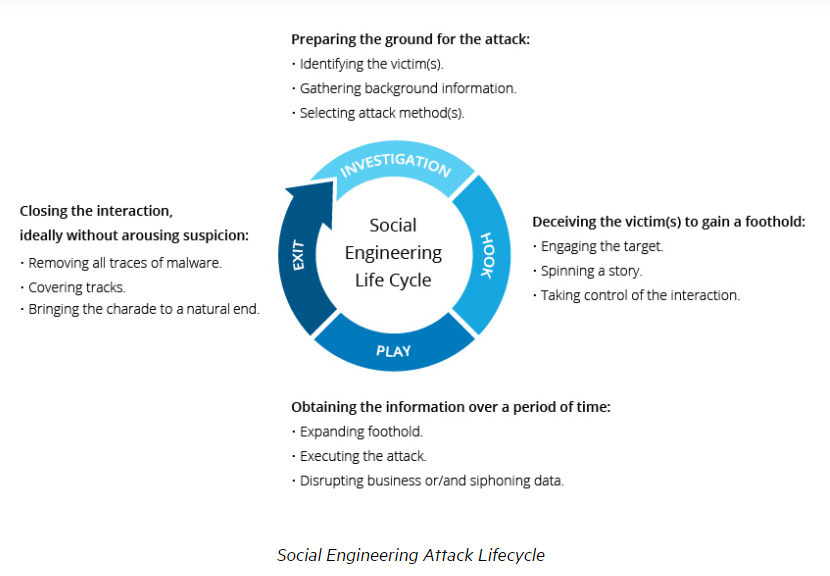
Social engineering attack techniques can be identified in five different forms such as;
- Baiting
Attackers leave baits often using physical gadgets. For instance, we hear stories like leaving malware-infected flash drives in places where potential victims (may be an employee of this company here) are certain to see them – especially on an office table / bathroom / elevator. The bait is attractive in a way that the bait has an authentic look to it, such as a label presenting it as the company’s ‘payroll list’ or ‘confidential’. These employees may just take the bait and insert the infected device into their company computers. Result of this is an automatic malware installation on the system. Sometimes baiting may take an online form too. For example, pop-up ads or messages carry infected links.
This makes people curious and may end up resulting in automatic malware installation on the system / computer.
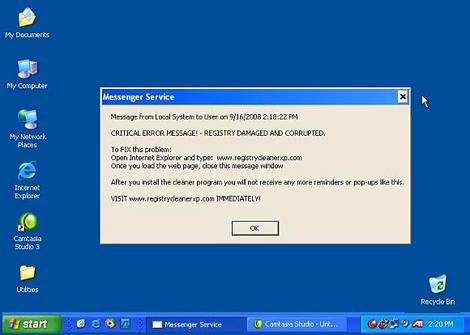
- Scareware
Scareware approaches victims, making them scared of something that is not real. For instance, you may get a message like
Warning – Your computer may be infected with harmful spyware programs
offering you to install a tool they recommend (most of the time, a malicious link)
- Pretexting
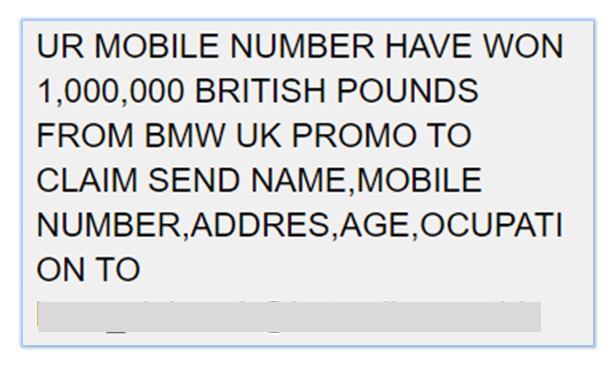 The attacker cleverly drafts lies pretending they have the authority to get your personal information such as phone numbers, bank account numbers, and Passport details. The words may come to you with the perfect logos, letterheads of the important officials to trick you.
The attacker cleverly drafts lies pretending they have the authority to get your personal information such as phone numbers, bank account numbers, and Passport details. The words may come to you with the perfect logos, letterheads of the important officials to trick you.
- Phishing
Scams attempting to take user credentials to hack your accounts and consequently blackmail, can be categorized as phishing.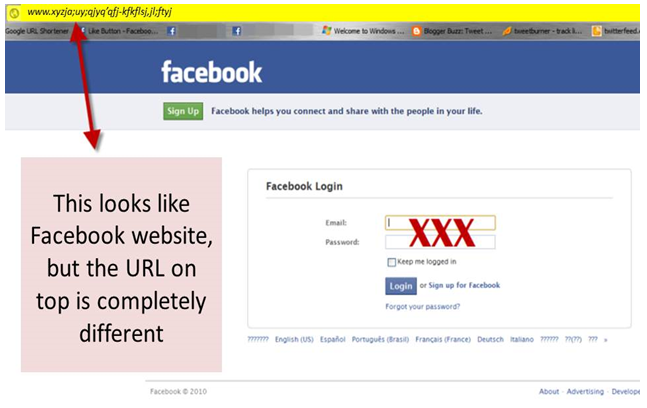 Find more information of how to identify which link is fake or real.
Find more information of how to identify which link is fake or real.
- Spear phishing
Spear phishing targets individuals skillfully. Social engineers spend more time and effort required to get someone caught as it is carefully aimed to the point, until the individuals believe that it is true and cannot escape responding. For example, hackers secretly attempt to convince people of lottery winnings or other unexpected price scams through emails asking for your personal information, which can be even used to do identity theft. Get to know about today’s top trending types of scams
Get to know about today’s top trending types of scams
Social engineering prevention
To prevent social engineers’ attacks, which manipulate human feelings; you should be on alert and think wisely before you react to anything on cyberspace.
Here are some tips to be secure from social engineering hacks;
- Do not open strange looking attachments or anything that contain enthusiastic links unless you make sure that the URL is correct. (Find out how to identify which link is fake or real)
- Use two-step authentication, which is a security process that uses two different authentication factors to verify the user. (Learn Two-step Authentication here)
- Never give your passwords or login credentials to anyone.
- Be wary of tempting offers, since they pave the way to lose even what you have.
- Install an up-to-date anti-virus / antimalware software
Learn more about Your Safety in Cyber Space.
References:
https://www.imperva.com/learn/application-security/social-engineering-attack/
https://www.pandasecurity.com/mediacenter/security/social-engineering/

